Today Microsoft released the Microsoft Office Isolated Conversion Environment (MOICE) tool or as we call it internally “the wringer”. This is to help mitigate unpatched security bugs in Office document parsing of the Office 97-2003 binary file formats (doc, ppt, pot, pps, xls, xlt, xla).A lot of security work was done as part of the Office 2007 product cycle. As a result, the file parsing in Office 2007 is more robust (and secure) than the previous versions of Office. (I’m not saying the Office 2007 parsers are perfect, but they are generally more robust and secure.) The MOICE tool allows the Office 2007 parsers to run on previous version of Office. Not only does it contain the stronger parsers, but the binary file format parsing runs with a restricted token. If malicious code does try to take advantage of a parsing bug in the wringer, it shouldn’t be able to drop a rootkit (the restricted token should prevent that).
How MOICE works
- MOICE is associated with the file extensions of concern. Normally Office file extensions are associated directly with the Office application of interest. For example, .doc is associated with winword.exe (Microsoft Word). Using the ASSOC tool included with the MOICE download, the file extension is associated with oice.exe. More on the associating is available in the knowledge base article - http://support.microsoft.com/?kbid=935865.
- Associated files now open with MOICE. MOICE parses the Office 97-2003 binary file and writes out a new file in the Office 2007 file format.
- ShellExecute occurs on the Office 2007 file. Since the Office 2007 file extensions are still associated with Office, this opens up the version of Office on the machine.
- Office opens the 2007 version of the file. The 2007 version of the file is understood because of the converter pack (allowing Office 2003 to read the Office 2007 file format).
Ways to bypass MOICE
By the description above, you might have noticed the way MOICE is invoked is by associating file Office 97-2003 extensions to it. There are other ways that files open in Office. These will bypass MOICE! For example, renaming a .doc file to .rtf will bypass MOICE and result in a .doc file opening in Word. (MOICE doesn’t associate itself with the rtf extension.) Another example of a MOICE bypass is if a file is opened by performing File->Open instead of double clicking the file. Clearly, you don’t want MOICE bypassed when you think you are using it.
How to prevent Office from parsing the document if MOICE is bypassed
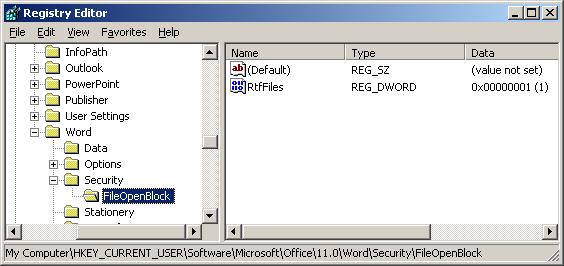
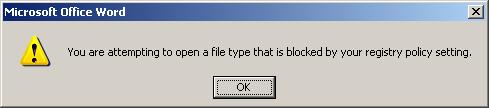
Since you cannot guarantee MOICE won’t be bypassed, you must prevent Office from directly opening the file formats you want MOICE to handle. This is done using the File Block feature I previous wrote about here. With File Block enabled, if a file bypasses MOICE and is one of the blocked types, the file will not be opened by Microsoft Office.
Labels: FileBlock, Microsoft Office, mitigation, MOICE, wringer
 Microsoft Press has translated Hunting Security Bugs to French under the title Chasser les failles de sécurité : Les meilleures pratiques pour tester la sécurité de vos logiciels. Here's a link to the French version on Amazon.fr -
Microsoft Press has translated Hunting Security Bugs to French under the title Chasser les failles de sécurité : Les meilleures pratiques pour tester la sécurité de vos logiciels. Here's a link to the French version on Amazon.fr -